- Solutions
- Partners
- Resources
- Blog
- GovCon Source
- GovCon Source Home
- Lean & Agile in the Age of DOGE
- Service Contract Act (SCA)
- DCAA Compliant Accounting
- GovCon Outsourcing & Managed Services
- Government ERP Systems
- Veteran-Owned Small Businesses
- GovCon CyberSecurity
- Graduating 8(a) Program
- SBIRs & Grants
- GovCon Growth Strategies
- GovCon Compliance Audits
- Webinars
- DCAA Compliance
- GovCon Accounting
- Graduating 8(a) Program
- Service Contract Act (SCA)
- GovCon Managed Services
- Government ERP Systems
- GovCon Reviews & Audits
- Cybersecurity Compliance
- Government Grants & Contracts
- Company
 Page Summary
Page Summary
Implementing a holistic cybersecurity program is essential for businesses to address data security challenges and regulatory standards like CMMC and NIST 800-171, involving assessment, planning, remediation, certification, and continuous monitoring. A comprehensive tool like CentrumCyber™ can streamline and optimize this process, ensuring long-term cybersecurity success and compliance.
In this blog, we will discuss the importance of Implementing a Cybersecurity Program. With the security challenges businesses are faced with today, data security is at the forefront of the conversation. Every business is struggling to implement the security measures to stay ahead of hackers looking to gain unauthorized access to sensitive user data, personal data, health records, intellectual property, control unclassified information (CUI), and credit card data. One thing that remains consistent is the need for businesses of all sizes to implement a holistic cybersecurity program to address these threats. Regulators have developed standards that must be followed to help ensure better security posture for their industries, but that alone turns into a check-box exercise with no real strategy. This is not a long-term solution and is not going to mitigate the amount of data breaches that occur. When it comes to addressing CMMC or NIST 800-171 implementing a programmatic approach to your cybersecurity practices is paramount to your future business success.
AtWork's Cybersecurity Keeps You Secure and Compliant
We provide cybersecurity protection services such as assessment, security program implementation,
and governance. Develop, execute, and maintain the cybersecurity to keep you protected and compliant.
and governance. Develop, execute, and maintain the cybersecurity to keep you protected and compliant.
Why Do I Need a Cybersecurity Program for my Business?
 When the newest regulation or executive order pertaining to cybersecurity are released, organizations tend not to act until an event occurs. When CMMC was first released there was a panic to submit a self-assessment causing some organizations to exaggerate their true SPRS Score. This wait-and-see approach carries enormous risks for the organization and can potentially subject the organization to other issues for falsifying information. Instead, organizations should look at cybersecurity as a program that needs to be established. Just like any other department within your organization, you need to have a systematic approach. Cybersecurity has lots of moving parts, not just data security, and you need to bring all stakeholders to the table to come up with an actionable plan to execute the business outcomes that are desired.
When the newest regulation or executive order pertaining to cybersecurity are released, organizations tend not to act until an event occurs. When CMMC was first released there was a panic to submit a self-assessment causing some organizations to exaggerate their true SPRS Score. This wait-and-see approach carries enormous risks for the organization and can potentially subject the organization to other issues for falsifying information. Instead, organizations should look at cybersecurity as a program that needs to be established. Just like any other department within your organization, you need to have a systematic approach. Cybersecurity has lots of moving parts, not just data security, and you need to bring all stakeholders to the table to come up with an actionable plan to execute the business outcomes that are desired.
Just Doing an Assessment is not Enough.
Assessments are a great place to start, providing a measuring stick against standards like CMMC and NIST 800-171. There is much more work to be done beyond the assessment and showing you are addressing deficiencies within your organization is what the DoD is looking to see. They understand that business has changed, how we communicate with others has changed and so is how we deal with privacy and security. If you want your organization to grow and prosper well into the future and win new government contracts, then you need to start thinking about how you improve your security and adopt a systematic approach. Assessments are just part of the process and not where the road ends. The clock is already ticking and it's a matter of time before CMMC is an official requirement to be awarded new DoD and other Federal contracts.
Basic Principles of a Cybersecurity Program
Let's think about how a cybersecurity program should be implemented based on how NIST (National Institute of Standards and Technology) describes the Cybersecurity Lifecycle. NIST CSF (Cybersecurity Framework) is a widely used approach to help identify and address the highest priority risks within your business. The NIST framework outlines you these five high-level steps for creating a comprehensive cybersecurity program; Identify, Protect, Detect, Respond, and Recover.
- Identify: Understand all your assets including equipment, software, and cloud providers. Understand who has or needs access, employees, vendors, and visitors.
- Protect: Implement safeguards to protect sensitive data while still providing the critical services required to conduct business operations.
- Detect: Monitor your infrastructure for potential cybersecurity events.
- Respond: Have a response plan when an incident is detected.
- Recover: Repair and restore data that has been compromised and inform the stakeholders.
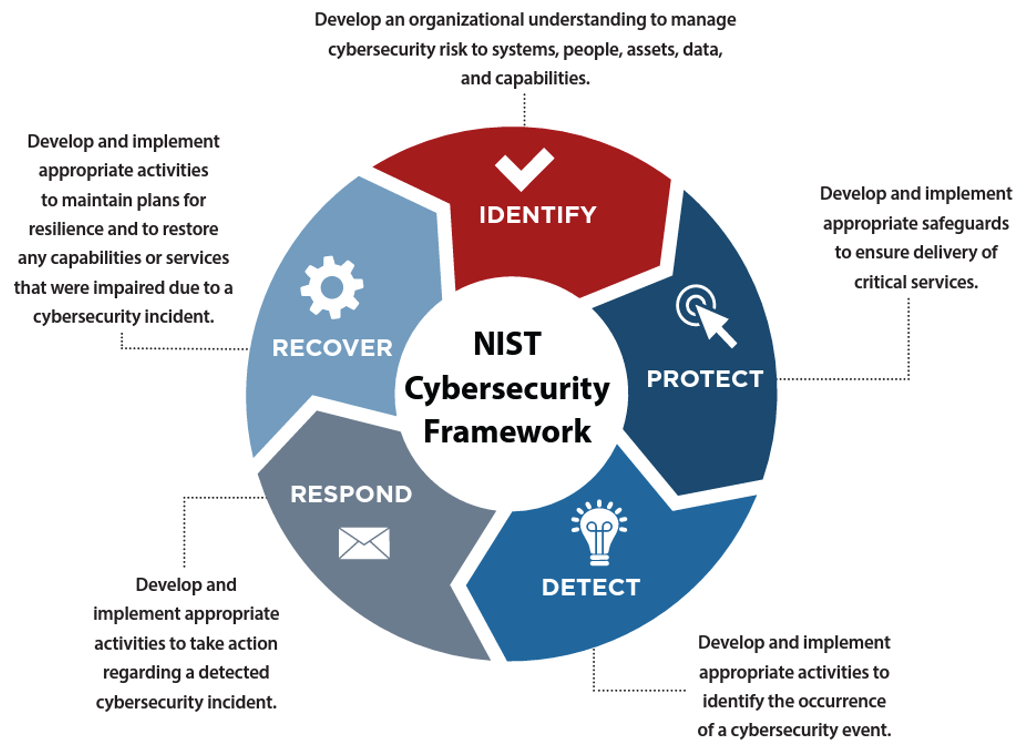
The NIST CSF is a good starting point and provides a high-level point of view, but it doesn't provide the details needed for your individual situation. The last two steps are also focused on responding to an incident and can be considered reactive approaches to address cybersecurity concerns. So how do you, 1. Be proactive, 2. Address compliance, 3. Understand the current risk within your organization 4. Monitor for threats 5. Make it a continuous process? Let's address these questions and outline a holistic approach.
Learn More: Utilizing Managed Services for Fractional CISO Support
Challenges that need to be Overcome
One of the most difficult challenges that cybersecurity professionals face today is that they are frequently siloed. It is viewed as a problem for the IT department rather than a business problem, and this is where everything falls apart. Consider who must be involved to address this complex issue. To begin, you must have an assessor who understands the frameworks, how to implement the controls in practice, and how you might have those implemented within your organization. There is also a remediator, which is the engineering team that is deploying those new solutions to address deficient controls or to perform the weekly, monthly, or yearly tasks required to maintain your level of compliance. Then there's the auditor, who is usually someone who isn't affiliated with the organization but requires some level of access to perform their duties. From start to finish, requires a great deal of coordination. We must now include the corporate stakeholders, the end users, and the management team. They typically want to know the status, where we are now in relation to the framework (CMMC, NIST), what plans are in place to close the gaps, as well as the budget of resources and costs to get the organization to the finish line. Furthermore, how will the changes affect the organization's operations, and how disruptive will the changes be?
As you can see, this is more than an IT issue and requires all siloed parties to collaborate to achieve the goal. Until now, these four areas (assessor, remediator, auditor, and organizational stakeholders) have operated in silos, with no real system in place to keep everyone informed. Implementing a holistic approach will assist in bringing these silos together, resulting in a collaborative cybersecurity program that provides effective business change.
A Holistic Cybersecurity Program Approach
Assess
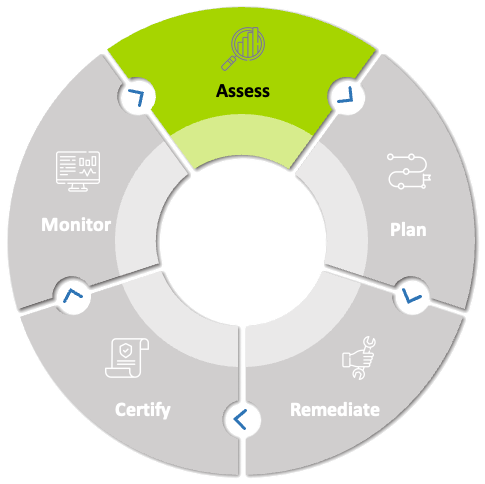 First as mentioned within NIST CSF, we must understand our assets, not just our IT assets, but our people, business processes, and potentially sensitive data within our organization. We must also define our cybersecurity boundary to know where the area of sensitive data (CUI) will reside.
First as mentioned within NIST CSF, we must understand our assets, not just our IT assets, but our people, business processes, and potentially sensitive data within our organization. We must also define our cybersecurity boundary to know where the area of sensitive data (CUI) will reside.
When addressing CMMC\NIST 800-171 the key is knowing your data and all systems that sensitive data might be resting on. Once these items are identified, you can then start to complete a baseline System Security Plan that outlines what NIST 800-171 controls you are currently addressing, what solutions you have in place, and what policies and procedures are present.
Plan
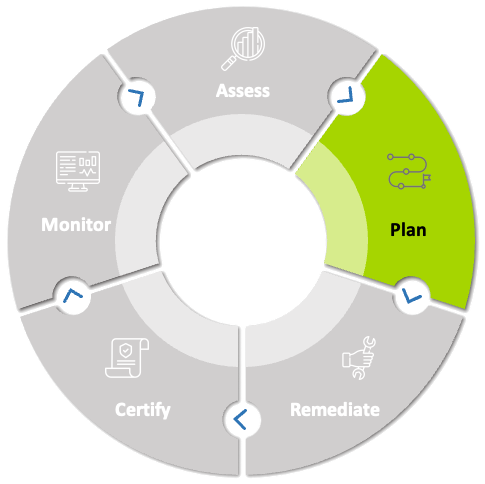 Once we have our NIST 800-171 baseline, we can now start to Plan our approach. We address the Protect section from the NIST CSF. This includes performing a gap assessment either internally or by an external 3 rd party against the baseline you have created. That assessment will yield "gaps" or security risks within the environment based on the control requirements found inside each NIST 800-171 control.
Once we have our NIST 800-171 baseline, we can now start to Plan our approach. We address the Protect section from the NIST CSF. This includes performing a gap assessment either internally or by an external 3 rd party against the baseline you have created. That assessment will yield "gaps" or security risks within the environment based on the control requirements found inside each NIST 800-171 control.
You will then use a source to align those gaps with solutions, practices, policies, or procedures that need to be implemented to satisfy them. You can't fix everything at once because of the potential effect on, productivity, culture, and operating changes. This is where the final part of the phase comes in, planning the actions to align with business needs, timelines, and budget. Having a road map to chart your journey is a critical part of improving and reducing your cybersecurity risk. Documenting a well thought out plan with discrete tasks and milestones is the key to success.
Also consider putting in place a PMO to coordinate and manage all the activities and stakeholder involved.
Remediate
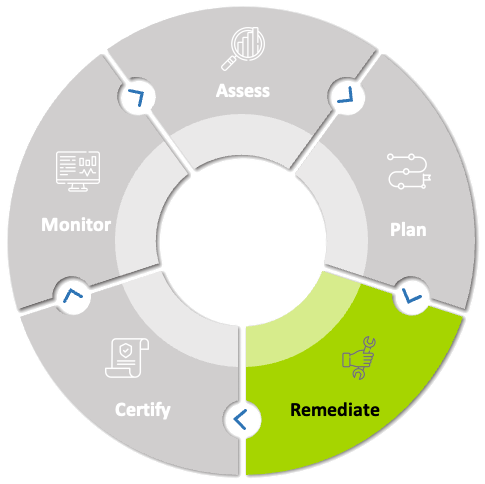 In the Remediate phase, we are going to implement the changes we have planned. This is where having a strong internal engineering team or a good implementation partner is going to be critical. All these changes take careful planning as they are most certainly going to cause disruption within your organization. This step also follows the NIST CSF Detect phase and includes developing and implementing appropriate activities to identify the occurrence of a cyber threat. New policies and procedures can also cause a change in culture but are a must to achieve CMMC\NIST compliance.
In the Remediate phase, we are going to implement the changes we have planned. This is where having a strong internal engineering team or a good implementation partner is going to be critical. All these changes take careful planning as they are most certainly going to cause disruption within your organization. This step also follows the NIST CSF Detect phase and includes developing and implementing appropriate activities to identify the occurrence of a cyber threat. New policies and procedures can also cause a change in culture but are a must to achieve CMMC\NIST compliance.
You could also work with a 3rd party vendor, a firm that specializes in system integration, and potentially a CISO to help bring it all together and manage the project delivery. Depending on the number of deficiencies you have within your organization, this could be the phase you spend the most time in. This is a process and it's important to show progress and improvements which means having the right team is critical. Another critical success factor is putting processes for managing governance, risks and compliance (GRC) as well as establishing a program management office (PMO) to track progress.
Certify
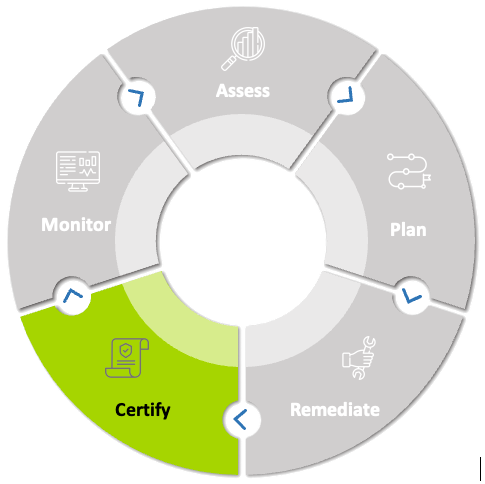 Organizations that create standards, like HITRUST, SOC, and ISO, have a process for obtaining certification for that standard. For CMMC, that would be the CyberAB which appoints specialized firms called C3PAOs that are certified to perform CMMC audits. Check with the appropriate parties for additional details and before you waste money and schedule an auditor to visit, it's a good idea to have a 3rd party prepare you for the event.
Organizations that create standards, like HITRUST, SOC, and ISO, have a process for obtaining certification for that standard. For CMMC, that would be the CyberAB which appoints specialized firms called C3PAOs that are certified to perform CMMC audits. Check with the appropriate parties for additional details and before you waste money and schedule an auditor to visit, it's a good idea to have a 3rd party prepare you for the event.
Additionally, if you seek outside assistance look for a firm that specializes in CMMC or NIST as they will know what the auditors will be looking for. This way, there are no surprises. You will have to perform an assessment yearly and recertify every 3 years. This fact is one of the most important factors in establishing a cybersecurity program, knowing that another audit is just 3 years away.
Once certified, CMMC certification will be valid for three years. Keep in mind, compliance isn't security, but compliance is a way to document what you've done to secure your environment. Without documentation if key personnel leave an organization, security can rapidly deteriorate, and complacency can set in. Documentation can provide the evidence and artifacts to demonstrate that certain security practices are in place. A document that clearly defines role-based access is an example of the type of policies and procedures that a contractor must have in place for level 2 certification.
Monitor
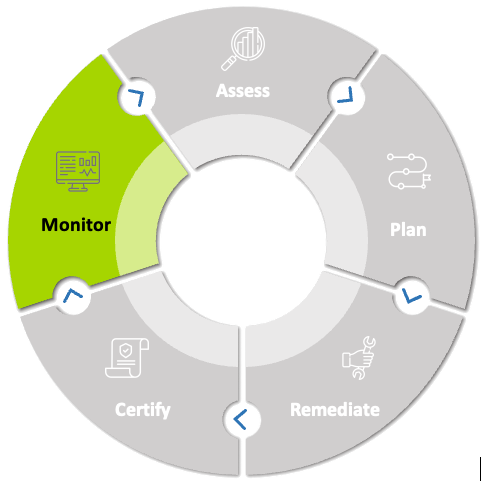 Maintaining your level of compliance and addressing issues in real-time are all part of monitoring your cybersecurity program. For CMMC you will need to recertify and reassess. You need to monitor your environment to ensure you maintain your certification, but also to adapt to new challenges within cybersecurity. We will also implement the last 2 phases of the NIST CSF framework within the phase.
Maintaining your level of compliance and addressing issues in real-time are all part of monitoring your cybersecurity program. For CMMC you will need to recertify and reassess. You need to monitor your environment to ensure you maintain your certification, but also to adapt to new challenges within cybersecurity. We will also implement the last 2 phases of the NIST CSF framework within the phase.
Some of the activities include responding to incidents, recovering from breaches, and improving our cybersecurity posture based on your findings. During this phase of the process, you will spend the most time maintaining your program ensuring risk is kept to an acceptable level while maintaining your current certification requirements.
As your business evolves so will your cybersecurity program and following this cycle will help you to maintain and improve your posture ensuring you maintain your CMMC certification. You can also achieve additional certifications and apply your current baseline to those requirements.
What tools are required to maintain your cybersecurity program?
After viewing the cybersecurity program model, one might wonder what tools are required to track it all. Most governance, risk, and compliance (GRC) platforms stop at the assessment or assess phase and offer little to no planning, project management, contouring monitoring, and access to all stakeholders. Further, they do not provide suggestions on how to remediate the gaps found within the assessment, which is a large hurdle in the process. Lastly, there is no roadmap on how to complete the process that includes, resources, time, budget, and a scorecard to measure progress along the way. Thus, leaving you stuck with separate systems, offline processes, and excel spreadsheets. All these offline processes are time-consuming and hard to track.
GRC solution that, provide traditional features as well as the ability to incorporate PMO functional are required to manage a holistic cybersecurity program. Tools such as CentrumCyber encompasses all these phases into one easy-to-use comprehensive SaaS platform. Centrum Cyber is a comprehensive SaaS platform that provides you with a single pane of glass to run and maintain your cybersecurity program. It follows the methodology described above allowing you to have predictable outcomes and establish a cybersecurity program for your organization.
This is no easy task and must be planned and executed appropriately to achieve and maintain CMMC certification. Taking the first step is always the most important one and if you have already started then great, you are on the right path. Regardless of your current program stage, even if you have just completed an assessment, Centrum Cyber can be a critical tool that will help you save money, achieve compliance faster and maintain a solid cybersecurity program for years to come.
